A number of local websites are failing to take a basic precaution to protect sensitive data moving between their website and their users. As a result, users who submit names, passwords, and personally identifying data are at risk of having that data intercepted and stolen by third-parties right now.
Fixing the problem takes only a few minutes and with certificates priced at less than £5 per year it is hard to justify not using HTTPS connections. HTTPS provides robust security and ensures user data in transit is secure from eavesdroppers.
Because we know password re-use is widespread, an attacker harvesting login credentials and cookies on a public network is able to leverage the attack to take over users’ accounts at other popular websites. This isn’t a theoretical concern - it happens frequently. The level of sophistication required to carry out this kind of attack is low and they are occurring more frequently.
If there is NO padlock in the browser window or ‘https://’ at the beginning of the web address to signify that it is using a secure link, do not enter personal information on the site. -getsafeonline.org
Put simply, an attacker using widely available free tools can sit at a local coffee shop and sniff your JEP login credentials, then try to re-use them on popular social media websites, online banking, and email services. Once an attacker has control of your email account she can use the “Forgot Password?” link elsewhere to exploit even more of your accounts.
Here I will illustrate exactly what is being done incorrectly and what must be done to fix the issue. I have used the Jersey Evening Post website for my example. Not because I wish to shame them, but because I like the Post and I want to see them improve security. I see the value in having a strong local Press and I know they can set a good example to others once they fix this vulnerability. (Readers should know I did contact them privately by email on 18th May to quietly bring this to their attention, and they chose not to reply.)
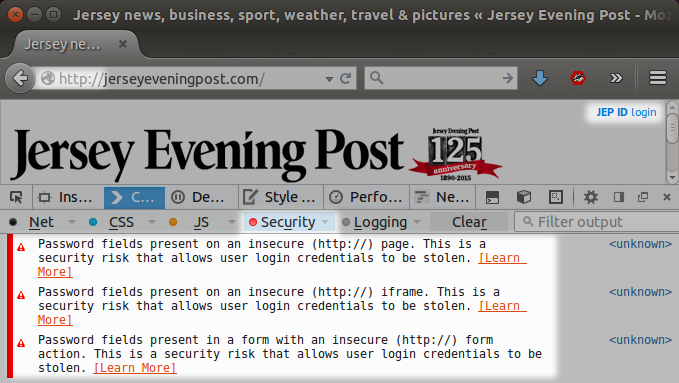
Screen-shot of Web Console security warning on Jersey Evening Post website.
Readers can visit jerseyeveningpost.com right now and test this, there is no need to take my word for it. Keyboard shortcuts vary by browser and operating system but if you are using Firefox, try Shift + Ctrl + K to open the Web Console. Once you arrive at their website you can then select or disable the different categories. Click on the “JEP ID Login” link at top right and watch the errors appear. In my screen-shot above I have disabled all but the Security category and shrunk the window size to keep things very simple.
If you want to dig a little deeper, you can inspect the page source (Ctrl + U in Firefox) and look for the form action in the HTML code. It will look like this: <form action="/myaccount" method="POST"> which on an unprotected site means “submit this form data in the clear”. Better is to have your site using HTTPS and best practice is to hard-code the secure link into the HTML form like so: <form action="https://www.example.com/myaccount" method="POST">.
Readers have little they can do to protect themselves right now. If you have an account at a website lacking HTTPS protection all you can do is make sure you use unique credentials for that site to limit damage from account hijacking. If you used the same email address and password for the JEP and for your email provider, you should change both passwords now and take care not to re-use passwords.
If you visit one of the JEP’s shopping websites like boutiquejersey.com or their restaurant guide jerseylovesfood.com you should know that all that personal information they ask you for in the registration forms is sent to them unprotected.
The website Get Safe Online is the UK’s leading source of unbiased, factual and easy-to-understand information on online safety and their advice on this is explicitly clear: If there is NO padlock in the browser window or ‘https://’ at the beginning of the web address to signify that it is using a secure link, do not enter personal information on the site.
The issue is hardly limited to the Evening Post’s family of websites. Plenty more examples exist throughout the Channel Islands, as you will likely hear about in the coming weeks.
If you are with the JEP and reading this feel free to contact me if you need help setting this up. I do this professionally and I am happy to point you in the right direction to get this resolved quickly and inexpensively. And as I stated in my email to you, I will purchase a subscription to read the paper online once I know you are protecting my login credentials. Or if you cannot do that, I cannot trust you with my personal data or my custom.
